IMPROVED SECURITY WITH CONTINUOUS TESTING AND HOLISTIC PROCESSES
enetration tests, or “pen tests” as they are typically called, are sometimes thought of as insurance policies for your network security. It is assumed that if you have undergone a penetration test, received a report, and fixed the issues discovered, you are secure and immune to devastating attacks.
OUR PENTESTING SERVICES:
Penetration testing
Why perform Penetration Testing? Validation of both internal and external security controls Simulation of existing threats using manual testing approach Simulation of common threats to organisations Testing of vulnerability detection capabilities Testing the response to identified threats
- External penetration testing
- Internal penetration testing
- Wireless penetration testing
- Web application assessments
- Mobile application assessments
- VPN testing
- VOIP and VLAN testing
- Firewall configuration and rule set reviews
- OS, Database and Webserver configuration reviews

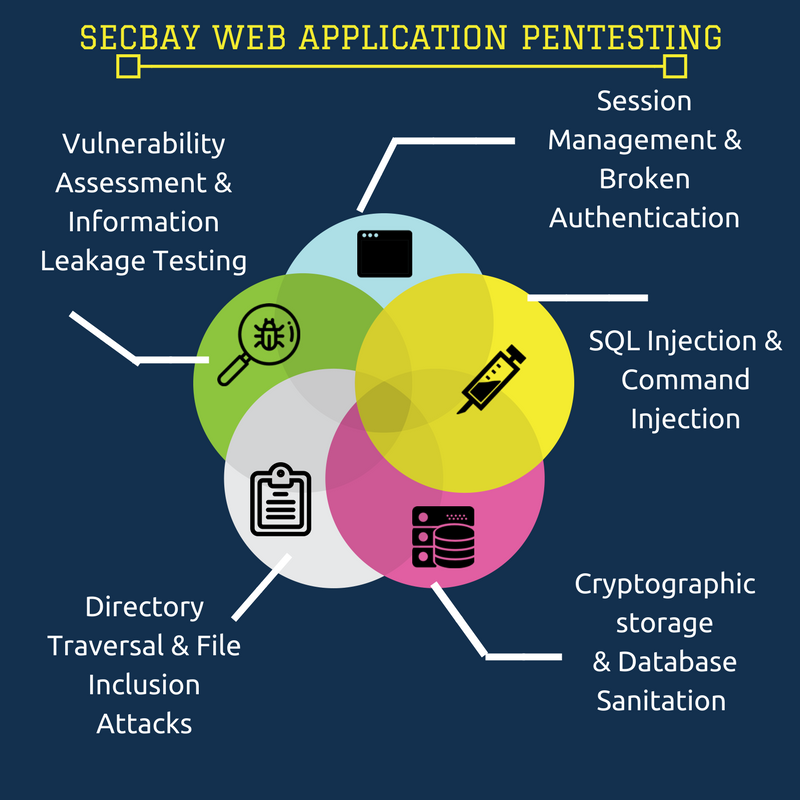
WEB APPLICATION PENTESTING
Web Applications present a potentially exploitable risk to your organization’s network. Ensure they are properly tested for possible vulnerabilities with our Web Application Penetration Testing methodology. Digital Boundary Group’s testing methodology determines if vulnerabilities exist in an application by testing application workflow, platform and host server.
ACCORDING TO OWASP TOP 10 WEB APPLICATION VULNERABILTIES :
- 1. Injection
- 2. Broken Authentication and Session Management
- 3. Sensitive Data Exposure
- 4. XML External Entity
- 5. Broken Access Control
- 6. Security Misconfiguration
- 7. Cross-Site Scripting
- 8. Insecure deserialization
- 9. Using Components With Known Vulnerabilities
- 10. Insufficient Logging and Monitoring
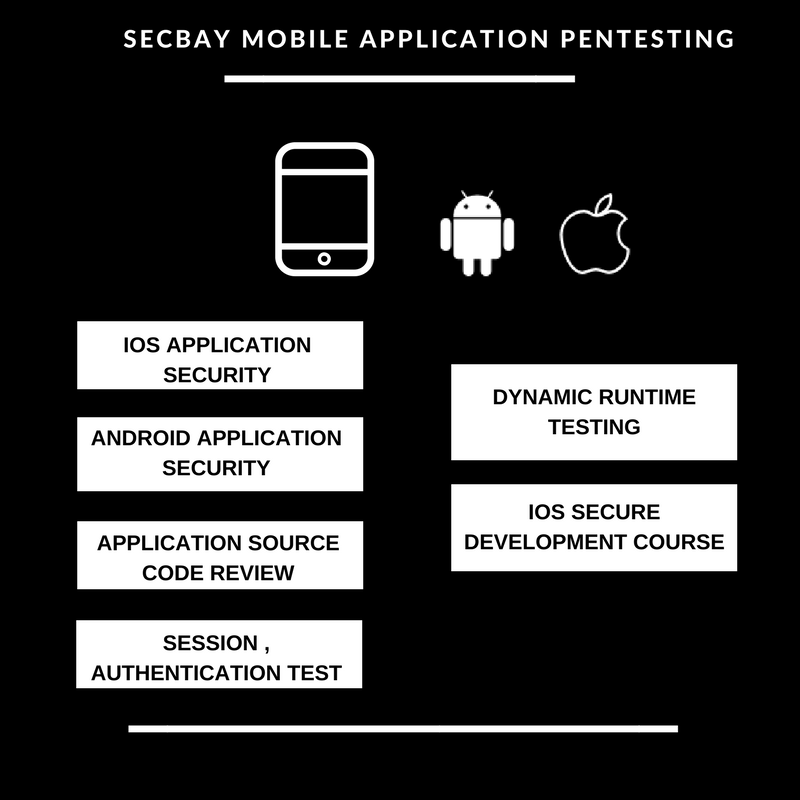
MOBILE APPLICATION PENTESTING
Mobile security analysts have a toolbox of multiple open source and third party tools they use to perform deep mobile app security assessments. Combining multiple open source tools takes too much time, creates inconsistent testing environments, and offers little in the way of unified reporting.
We carry out Mobile Application in phases, so we follow industry standards
Our Approach:
PHASE 1: INFORMATION RECONNAISSANCE
PHASE 2: THREAT MODELLING
PHASE 3: EXPLOITATION
PHASE 4: DYNAMIC RUNTIME ANALYSIS
PHASE 5: REPORTING
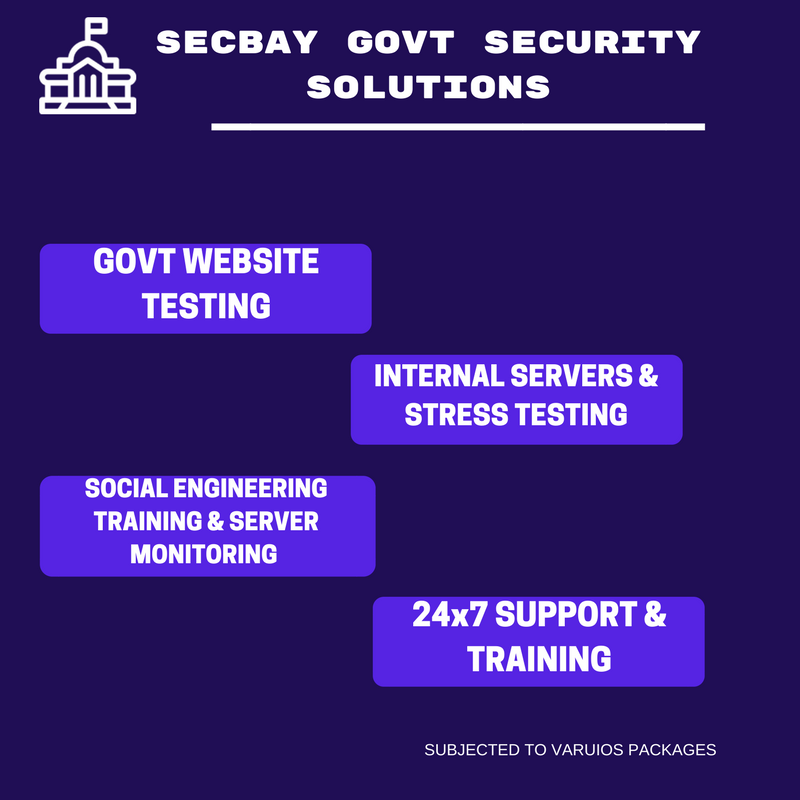
GOVT SERVER & WEBSITE SECURITY
Web, email and mobile applications are increasingly targets of attack, making it necessary to advance your defenses beyond network and endpoint protection. We can assist your organization with these challenges by reviewing application policy, procedures and architecture, and design to identify immediate technical vulnerabilities. We can also evaluate and help optimize your non-technical controls that can impact security over time.
We Provide Expert Advisory & Consultation in the areas of
-
Cyber Security Assessment & Monitoring
-
WebSite & WebServer Vulnerability Scanning & Penetration Testing
-
WebServer DDOS Protection
-
System & Endpoint protection & Ransomware Monitoring
-
PostAttack Forensics & Consultations
-
Mobile / HDD/ SDD Forensic Consultation
-
Law Enforcement Specialized Training
-
Law Enforcement Consultation Services
-
Anti-Phishing & Biometric Security Services
SECBAY VAPT PHASES

We are available 24x7 for you
Talk to a Secbay security expert today and find out how we can help you!